Bug #4018
closed
typeahead: long query parameter / answer triggers 'Attack detected' and purges current SIP storage.
Added by Carsten Rose almost 7 years ago.
Updated over 1 year ago.
Description
- maybe a post request?
- Problem was #4009
Situation:
- User loads form
- use typeahead against uzh webpass
- shortname as column
- user save and close record
- user open form with saved record again
- form loads
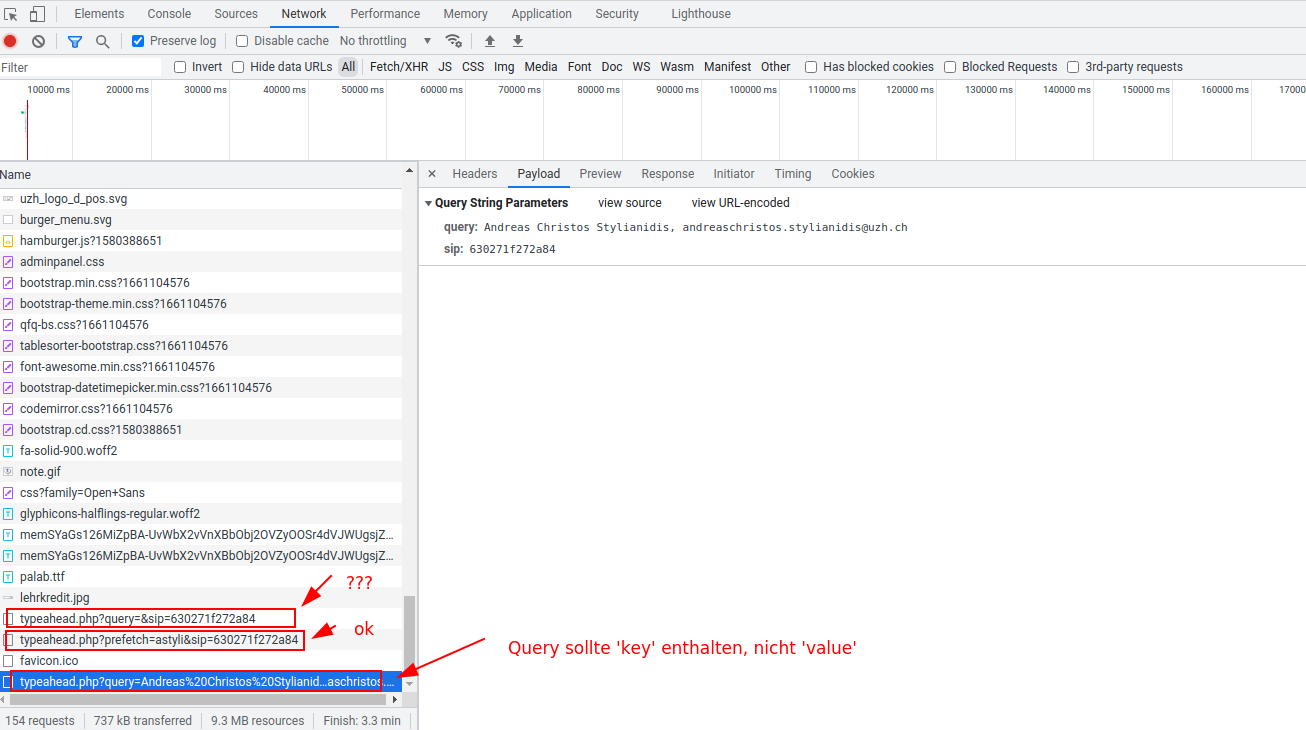
- typeAheadLdapSearchPrefetch: typeahead fires a query after form load to display expanded LDAP search query. for this it uses the expanded value. this is not clear to CR why.
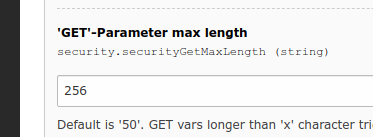
- The expanded value exceeds the SECURITY_GET_MAX_LENGTH of 50.
Files
- Target version set to next9
- Status changed from New to Some day maybe
- File clipboard-202206292238-xftuq.png clipboard-202206292238-xftuq.png added
- Subject changed from typeahead: solve problem with potential long query parameter to typeahead: long query parameter / answer triggers 'Attack detected' and purges current SIP storage.
- Status changed from Some day maybe to New
- Target version changed from next9 to 355
- Das duerfte auch das Problem in #14440 gewesen sein.
- Beim laden des Forms wurde die eingestellte Security.MaxLength uberschritten
- Effekt: das Form konnte geladen werden, danach war aber die SIP kaputt! Erst bei dem naechsten Klick auf z.B. einen SIP kodierten Button, oder wenn man einfach Reload (F5) gedrueckt hat, hat QFQ gemeldet 'invalid SIP'.
Steps:
- Wenn QFQ merkt 'oops, attack detected' - dann sollte QFQ das auch dem Benutzer mitteilen oder z.B. im Log etwas notieren.
- Das hochsetzen von `security.securityGetMaxLength` ist schlecht. TypeAhead Felder sollten einen eigenen Mechanismus bekommen, damit sie automatisch die maximale Laenge vertragen. Sollte bei einem SQL / LDAP Answer mehr geliefert werden, einfach abschneiden, keinen Fehler produzieren! Es gibt bereits eine Moeglihckeit das Feldnamen eine individuelle MaxLength bekomen '256_StandGeschaeft' z.B.. Dies koennte automatisch gesetzt werden bei TypeAhead Feldern.
- Wenn der Bug behoben ist, sollten alle QFQ Instanzen zurueck auf 50 Chars gesetzt werden.
- Related to Bug #9077: typeAheadSql: report broken SQL added
- Related to Bug #5788: DoS-String für TypeAHead added
- Tracker changed from Feature to Bug
- Status changed from New to In Progress
- Prio Planung set to No
- Target version changed from 355 to 385
- Den Parameter TYPEAHEAD_API_MAX_LENGTH = 512; gab es schon laenger - aber scheinbar war der nicht aktiv (Fehler in der Programmierung)
- Neu werden GET-Parameter TYPEAHEAD_API_QUERY und TYPEAHEAD_API_PREFETCH begrenzt auf TYPEAHEAD_API_MAX_LENGTH - das sollte reichen.
- Target version changed from 385 to 24.10.0
Check ob das nicht schon lange gefixt ist
- Assignee changed from Carsten Rose to Enis Nuredini
- Status changed from In Progress to ToDo
- Status changed from ToDo to Priorize
- Target version changed from 24.10.0 to 411
- Target version changed from 411 to 22.12.1
- Status changed from Priorize to Closed
- Target version changed from 22.12.1 to 22.8.0
Also available in: Atom
PDF